Without these tools implementing deep. And social good health energy.
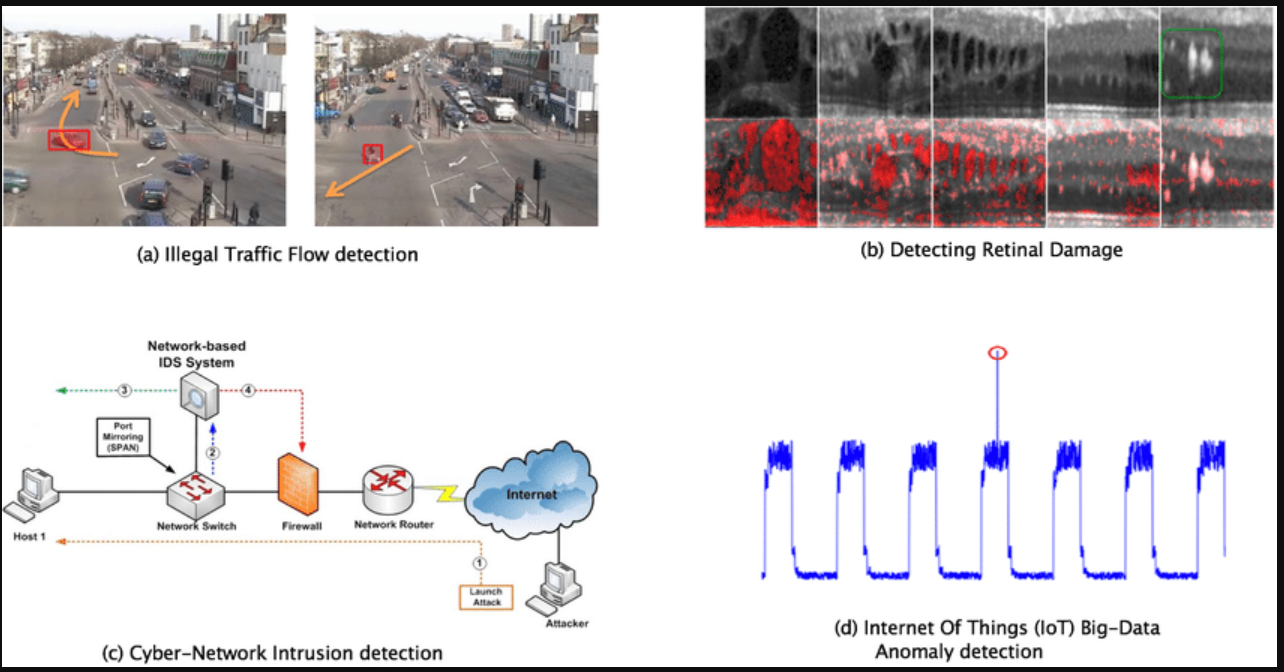
Real Time Anomaly Detection A Deep Learning Approach By Abacus Ai Abacus Ai Blog Formerly Realityengines Ai Medium
Large graph visualization and mining.

. Networking is the construction design and use of a network that includes cabling hub bridge switch router and so forth. Most of the IEEE Networking Projects are done by java programming. The entire chip is just 93 square millimeters in size.
Who has been outspoken about Donald Trump and Trumps threat to democracy announces September 2 is his last day. The new device marks the first deep neural network implemented entirely on an integrated photonic device in a scalable manner. Keywords IoT malicious attacks feature selection unsupervised ensemble learning deep learning 1 Introduction The Internet of Things IoT expands the Internets edge by integrating.
ABC NBC and CBS declined to air Bidens prime-time speech about democracy and extremism. DBN Deep Belief Network outperform the other models with a detection accuracy of 975 and a false alarm rate of 23 when trained using labelled dataset supplied by the proposed approach. Paul Farhi Washington Post.
Our current research thrusts. In a recurrent neural network RNN the signal will propagate through a layer more than once. ED raids Paytm Razorpay Cashfree Payments in Chinese loan app case.
CSE Projects ECE Projects Description Networking Projects. Aroon Deep Entrackr. Deep-learning frameworks bring together everything needed to design train and validate deep neural networks through a high-level programming interface.
RNNs can be trained by gradient descent 139 however long-term gradients which are back-propagated can vanish that is they can tend to zero or explode that is they can tend to infinity known as the vanishing gradient problem. Human-centered AI interpretable fair safe AI. Thus an RNN is an example of deep learning.
ElysiumPro offers an extensive list of project ideas on Networking for students. At Georgia Tech we innovate scalable interactive and interpretable tools that amplify humans ability to understand and interact with billion-scale data and machine learning models. Detect DGA domains of modern malware using deep neural networks Leverages machine learning for URL grouping and tokenization to increase web filtering coverage Prevents known threats and delivers immediate insights into the type of specific security risks with 16.
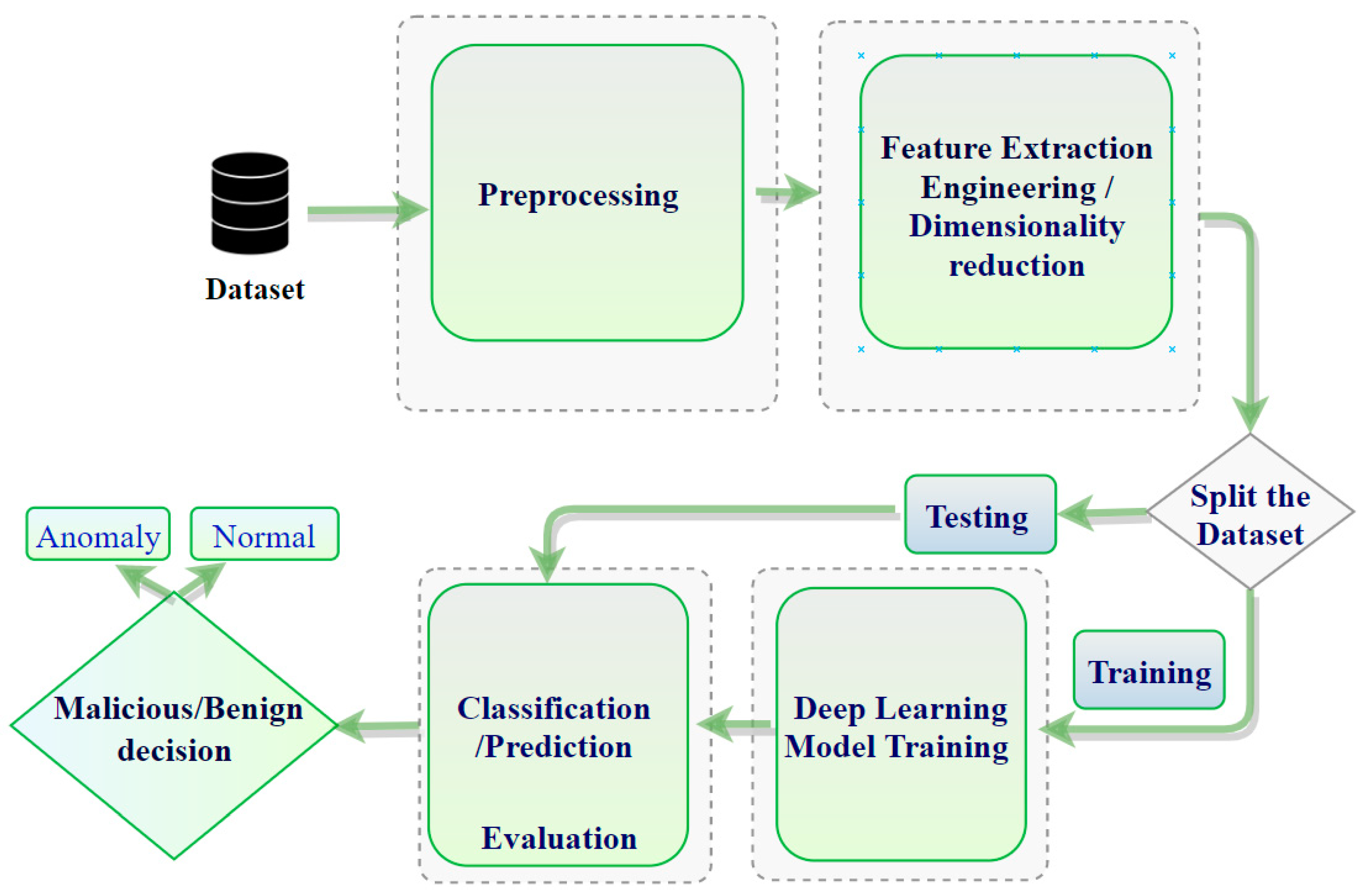
Sensors Free Full Text Iot Intrusion Detection Taxonomy Reference Architecture And Analyses Html
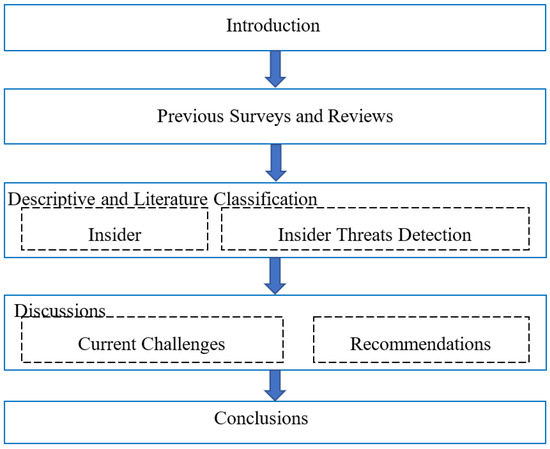
Applied Sciences Free Full Text A Review Of Insider Threat Detection Classification Machine Learning Techniques Datasets Open Challenges And Recommendations Html

Insider Threat Detection With Deep Neural Network Springerlink

Unauthorized Access Account Takeover Insider Threats Accounting Threat Data Breach
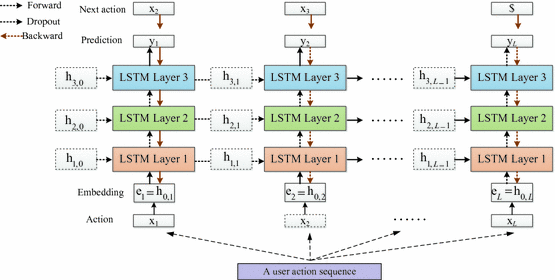
Insider Threat Detection With Deep Neural Network Springerlink
Deep Learning Neural Network Download Scientific Diagram

Deep Learning For Anomaly Detection
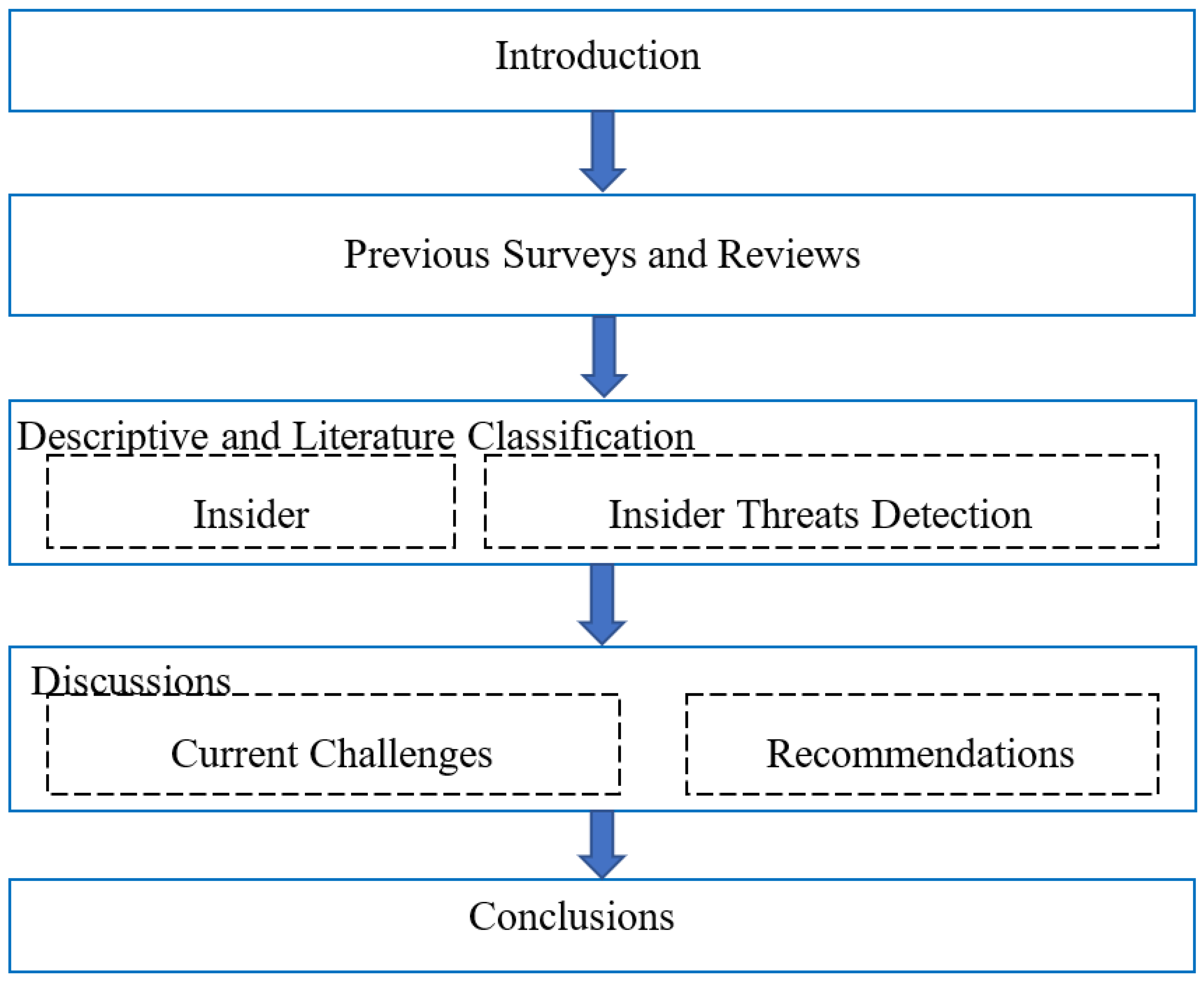
Applied Sciences Free Full Text A Review Of Insider Threat Detection Classification Machine Learning Techniques Datasets Open Challenges And Recommendations Html
0 comments
Post a Comment